Xbox 360 Kernel: Difference between revisions
No edit summary |
|||
| (45 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
== Boot-up == | == Boot-up == | ||
TheSpecialist, Xboxhacker.net: | TheSpecialist, Xboxhacker.net [http://www.xboxhacker.net/index.php?topic=7692.msg47935#msg47935]: | ||
Well from power-on: | Well from power-on: | ||
1. 1BL (first bootloader, stored in ROM), this loads decrypts and starts: | 1. 1BL (first bootloader, stored in CPU ROM), this loads decrypts and starts: | ||
2. CB (2BL, 2nd bootloader, stored in NAND), this this loads decrypts and starts: | 2. CB (2BL, 2nd bootloader, stored in NAND), this this loads decrypts and starts: | ||
3. CD. This loads, decrypts and decompresses CE, which contains the base kernel + base HV (Hypervisor). | 3. CD. This loads, decrypts and decompresses CE, which contains the base kernel + base HV (Hypervisor). | ||
| Line 12: | Line 12: | ||
Every step also checks signature for the next step of course. | Every step also checks signature for the next step of course. | ||
Keyvault is decrypted by the Hypervisor using the CPU Key [http://www.xboxhacker.net/index.php?topic=7872.msg50718#msg50718]. | |||
== Crypto structure == | |||
Arnezami's summary of the different crypto hashes [http://www.xboxhacker.net/index.php?topic=8668.msg55035#msg55035]: | |||
There are 3 kinds of verification used during boot: | |||
- RSA signatures. CB and CF are RSA signed. No way to break this (MS has private key) basicly because it uses | |||
assymetric crypto. This prevents us from changing the boot code itself. | |||
- SHA1 hash: CD, CE, CG. These hashes are contained in the RSA signed part of the previous sections and we | |||
can therefore not break it (also not time attackable). These can essentially be seen as extentions of the RSA | |||
signatures in CB and CF. Again preventing us from modyfing the boot code itself. | |||
- SHA1-HMAC authentication. This is done in CB and CF too (but your CPU has the key). This prevents you to | |||
choose between released versions of the boot sections/dash etc. However this was time attackable. | |||
== Dump Data == | |||
There are 3 essential parts of data you want to dump from the Xbox 360; the NAND flash, the fusesets, and the 1BL first bootloader. The former located in the [http://www.free60.org/wiki/Flash HYNIX HY27US08281A] flash and the two latter in the [http://www.free60.org/wiki/CPU IBM PowerPC Xeon CPU]. | |||
=== NAND === | |||
There are two ways to get the NAND flash: | |||
* Physically read the flash using the Infectus NAND Microchip Flasher | |||
* Dump it from memory using the King Kong Exploit and Linux | |||
=== Fusesets and 1BL === | |||
These two can only be dumped using Linux. Follow the 'Linux' section below to extract the parts. | |||
=== Dumping === | |||
==== Infectus ==== | |||
* [[Xbox 360 NAND|Guide how to dump the flash using Infectus]] | |||
==== Linux ==== | |||
Start by upgrading to a vulnerable kernel, 4532 or 4548, and patch the King Kong game ISO to load the XeLL loader from a LiveCD, [[King Kong Shader Exploit|here]]. | |||
There are two different ways to dump the necessary data, one with dump32 to get the 1BL, CPU Key and NAND dump, and the other tmbincdump to get the true NAND dump with the correct ECC values. | |||
===== dump32 ===== | |||
When Linux is loaded, start one of the webbrowsers (assuming you have a network cable plugged in) and browse to this page to download [http://www.xboxhacker.net/index.php?topic=7913.msg50090#msg50090 arnezami's dump32.c] ([http://beta.ivancover.com/xbox360/files/arnezamidump32.tgz mirror]). Save it to the desktop. | |||
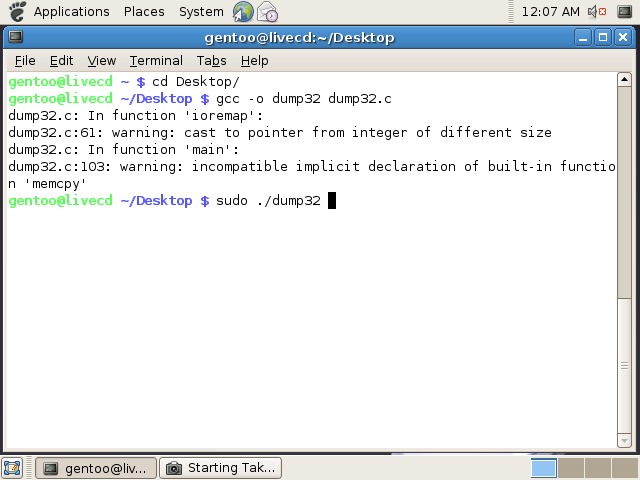
Open a new Terminal from the menus, and 'cd Desktop'. Now compile the dump32 using the following command: | |||
gcc -o dump32 dump32.c | |||
[[Image:Dump32 Compile and Start.png]] | |||
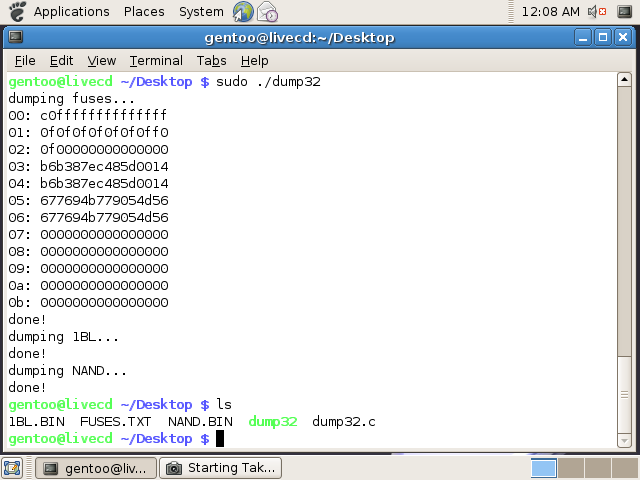
As shown, now execute the application by typing 'sudo ./dump32'. Make sure to make it executable by typing 'chmod +x' first. The application will now dump the fuses, 1bl and NAND to the current directory. | |||
sudo ./dump32 | |||
[[Image:Dump32 Finished and List.png]] | |||
Backup these files to another computer through SCP, USB pen, website upload, FTP transter, or similar. I used SCP to another Mac OS X machine: | |||
scp 1BL.BIN FUSES.TXT NAND.BIN torsten@192.168.1.3: | |||
To SCP in from a Windows machine, download WinSCP and set a password for the root account with 'sudo passwd' and enter a password. Find the IP address of the 360 using the network tool from the menus. | |||
===== tmbincdump ===== | |||
Get the [http://www.xboxhacker.net/index.php?topic=7290.msg52510#msg52510 tmbinc code] ([http://beta.ivancover.com/xbox360/files/tmbincdump.tgz mirror]) and save it to the desktop as tmbincdump.c. You have to change the writereg command from: | |||
writereg(COMMAND, 2); | |||
to: | |||
writereg(COMMAND, 3); | |||
This enables the correct mode to dump the NAND flash. Mode 2 shows all the blank and empty banks, while mode 3 only dumps the necessary data and auto corrects for bad blocks. | |||
Compile it using: | |||
gcc -I=/usr/include/ -O -o tmbincdump tmbincdump.c | |||
Now execute the dumper: | |||
sudo ./tmbincdump | |||
The complete dump will be saved to a file named tmbincdump.bin. Transfer this to a computer using one of the methods referred to | |||
== View Content == | == View Content == | ||
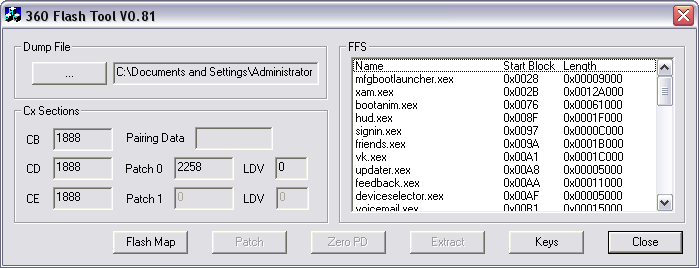
To view the content of the dumped NAND flash download the latest version of [http://www.xboxhacker.net/index.php?topic=7691.0 360 Flash Dump Tool] and open the BIN file. | To view the content of the dumped NAND flash download the latest version of [http://www.xboxhacker.net/index.php?topic=7691.0 360 Flash Dump Tool] and open the BIN file. | ||
To decode all of the encrypted content you need the CPU Key located in the fusesets | To decode all of the encrypted content you need the CPU Key located in the fusesets and the 1BL Key located in the CPU ROM. These are found using the King Kong shader exploit and XeLL (Xeon Linux Loader) on vulnerable firmware version, e.g 4532 and 4548, as shown above. | ||
[[Image:360 Flash Dump Tool.PNG]] | [[Image:360 Flash Dump Tool.PNG]] | ||
| Line 29: | Line 100: | ||
0x8000_0200_0001_0000 and key is 0x10 bytes long. %rtoc is 0. Don't get sidetracked digging too deeply into each and | 0x8000_0200_0001_0000 and key is 0x10 bytes long. %rtoc is 0. Don't get sidetracked digging too deeply into each and | ||
every bl off sub_4240. | every bl off sub_4240. | ||
To figure out if you've found the correct key, open 360 Flash Dump Tool, enter the key, and check if there's a 'Pairing Data' entry. | |||
== Fuses == | == Fuses == | ||
There are 12 fusesets and they form the fundament for the Xbox 360 hypervisor security [http://www.xboxhacker.net/index.php?topic=7691.msg49343#msg49343]. | There are 12 fusesets and they form the fundament for the Xbox 360 hypervisor security [http://www.xboxhacker.net/index.php?topic=7691.msg49343#msg49343]. The fusesets (12) are located inside the CPU and thus hard to modify externally. | ||
Fuseset #01 - 00: c0ffffffffffffff | Fuseset #01 - 00: c0ffffffffffffff | ||
| Line 46: | Line 119: | ||
Fuseset #12 - 0b: 0000000000000000 | Fuseset #12 - 0b: 0000000000000000 | ||
=== CPU Key === | For a description of what the purpose of each set, see this [http://www.xboxhacker.net/index.php?topic=7389.msg47673#msg47673 thread post]. | ||
=== CPU / Per-Box Key === | |||
The CPU Key is used to only encrypt the Keyvault (which is then encrypted by the 1BL Key). By altering the the Keyvault you can change the lockdown counter on a vulnerable kernel, re-encrypting the Keyvault with the CPU Key, and downgrading to vulnerable kernel by flashing the NAND. A prior NAND dump from a vulnerable kernel is still needed and you have to already acquired the CPU Key using the King Kong exploit. | |||
It is now possible to downgrade to a vulnerable kernel by time attacking the hash value of the lockdown counter. The counter is unsigned and the hash is compared bytewise. | |||
* [[Xbox 360 Timing Attack]] | |||
The CPU Key can be found by combining fusetset #03 + #05 (or #04 + #06). The final string should be 16 bytes long, e.g xxxxxxxxxxxxxxxxyyyyyyyyyyyyyyyy. | The CPU Key can be found by combining fusetset #03 + #05 (or #04 + #06). The final string should be 16 bytes long, e.g xxxxxxxxxxxxxxxxyyyyyyyyyyyyyyyy. | ||
To extract the fusesets use XeLL (shown below) or [http://www.xboxhacker.net/index.php?topic=7913.msg50090#msg50090 arnezami's dump32]. | |||
=== XeLL Output === | |||
This shows the XeLL output | This shows the XeLL output from the serial cable method. | ||
Xe>! | Xe>! | ||
XeLL - Xenon linux loader 0.1 | XeLL - Xenon linux loader 0.1 | ||
| Line 84: | Line 165: | ||
fuseset 10: 0000000000000000 | fuseset 10: 0000000000000000 | ||
fuseset 11: 0000000000000000 | fuseset 11: 0000000000000000 | ||
== Keyvault == | |||
The Keyvault contains unsigned information about the system, like serial number, manufacture date, DVD key, certificates, etc. It's encrypted by the CPU Key. | |||
* [http://www.xboxhacker.net/index.php?topic=7872.0 Keyvault list] | |||
== Downgrade == | == Downgrade == | ||
Downgrading is restricted by changing a lockdown counter in the NAND and the value of a | Downgrading is restricted by changing a lockdown counter in the NAND and the value of a fuseset. If these two don't match, e.g lockdown counter is lower than the value of the fuseset, the machine refuses to boot. It's possible to disable the change of the fuseset by removing power the the fuse and essentially disabling it. [[Xbox 360 NAND|More about how to remove the R6T3 resistor]]. | ||
It's possible to disable the change of the fuseset by removing power the the fuse and essentially disabling it. | |||
It is still possible to downgrade if the fuseset has increased, but it requires CPU Key and altering of the old NAND dump to increase the lockdown counter. (As of 9th Aug. 2007 the CPU Key can only be found on a exploitable 4532 or 4548 system). | It is still possible to downgrade if the fuseset has increased, but it requires CPU Key and altering of the old NAND dump to increase the lockdown counter. (As of 9th Aug. 2007 the CPU Key can only be found on a exploitable 4532 or 4548 system). | ||
=== Counters === | === Counters === | ||
While upgrading to | While upgrading to 4532 or 4552, fuseset #07 is changed and the lockdown counter in the NAND is increase by 1, for each update. I.e.: | ||
Stock 2241: | Stock 2241: | ||
Lockdown counter: 0 | Lockdown counter: 0 | ||
| Line 109: | Line 193: | ||
To bypass this you need to decrypt the CF section of the 4532 dump and change the byte at 0x21F to something higher. The 360 Flash Dump Tool will patch and properly re-encrypt the flash image. | To bypass this you need to decrypt the CF section of the 4532 dump and change the byte at 0x21F to something higher. The 360 Flash Dump Tool will patch and properly re-encrypt the flash image. | ||
== Region code == | |||
It's possible make a PAL system act as a NTSC system, and vice versa, by changing the region bit in the Keyvault [http://www.xboxhacker.net/index.php?topic=7872.msg51233#msg51233]. | |||
1. Dump the NAND from the US 360 (528-bytes-per-page) | |||
2. Open in the latest flashtool (v0.8 ) and click [extract] | |||
3. Edit extracted KV.bin and change 16-bits at offset 0xB8 from 0x00FF (NTSC) to 0x02FE (PAL) | |||
4. Open in flashtool and click [patch], check the "patch keyvault" box and select the KV.bin modified in step 3 | |||
5. Click [OK] and choose output file | |||
6. Flash output image back to the NAND of the US 360 | |||
7. Try an EU game or two. | |||
Apparently you need both the 1BL and CPU Key to perform this with 360 Flash Dump Tool v0.8. | |||
Region codes [http://gueux-forum.net/index.php?showtopic=167835]: | |||
- PAL : il faut changer ces 4 chiffres en 02FE | |||
- NTSC/J : il faut changer ces 4 chiffres en 01FF | |||
- NTSC-U/C : il faut changer ces 4 chiffres en 00FF | |||
- NTSC/KOR : il faut changer ces 4 chiffres en 01FC | |||
== Future hacks == | |||
# Downgrade allowed via timing attack for all current machines, as of 2007-08-19 / kernel 5766 [http://www.xboxhacker.net/index.php?topic=8319.msg52753#msg52753] | |||
# Dual kernels via switches or xD cards, one for exploitable kernel (4532 or 4548), another for Xbox Live/latest kernel | |||
# King Kong game required to boot homebrew | |||
# Find kernel exploits in 4532 or 4548 to make an on-boot exploit to not require King Kong | |||
== References == | == References == | ||
| Line 119: | Line 228: | ||
* [http://www.xboxhacker.net/index.php?topic=7913.msg50090#msg50090 arnezami's dump32.c dump tool] | * [http://www.xboxhacker.net/index.php?topic=7913.msg50090#msg50090 arnezami's dump32.c dump tool] | ||
* [http://www.xboxhacker.net/index.php?topic=7290.msg51330#msg51330 tmbinc's flash read dump tool] | * [http://www.xboxhacker.net/index.php?topic=7290.msg51330#msg51330 tmbinc's flash read dump tool] | ||
* [http://www.xboxhacker.net/index.php?topic=7290.msg52510#msg52510 atiman edition of tmbinc's dump tool] | |||
* [http://www.xboxhacker.net/index.php?topic=7691.msg50039#msg50039 Keyvault encrypted by CPU Key] | |||
* [http://www.xboxhacker.net/index.php?topic=7872.0 Keyvault Content] | |||
* [http://www.xboxhacker.net/index.php?topic=7872.msg50718#msg50718 Keyvault decrypted by Hypervisor] | |||
* [http://www.xboxhacker.net/index.php?topic=7872.msg51233#msg51233 Changing DVD Key and Region code] | |||
* [http://www.xboxhacker.net/index.php?topic=8319.20 Timing Attack - Stupid Question] | |||
* [http://www.eurasia.nu/wiki/index.php?pagename=Xbox360Info Eurasia Xbox 360 Wiki] | |||
* [http://www.xboxhacker.net/index.php?topic=6674.0 Layout of the 16mb NAND] | |||
* [http://gueux-forum.net/index.php?showtopic=167835 Change region code] | |||
Latest revision as of 10:53, 14 March 2009
Boot-up
TheSpecialist, Xboxhacker.net [1]:
Well from power-on: 1. 1BL (first bootloader, stored in CPU ROM), this loads decrypts and starts: 2. CB (2BL, 2nd bootloader, stored in NAND), this this loads decrypts and starts: 3. CD. This loads, decrypts and decompresses CE, which contains the base kernel + base HV (Hypervisor). It also loads decrypts and then starts: 4. CF. This loads, decrypts and decompresses CG, which contains the patches for kernel and HV. It then applies the patches and starts up the patched HV and then the patched kernel. Then it boots dash. So basically it's like: 1BL -> 2BL -> patch kernel and HV and start them -> boot dashboard. Every step also checks signature for the next step of course.
Keyvault is decrypted by the Hypervisor using the CPU Key [2].
Crypto structure
Arnezami's summary of the different crypto hashes [3]:
There are 3 kinds of verification used during boot: - RSA signatures. CB and CF are RSA signed. No way to break this (MS has private key) basicly because it uses assymetric crypto. This prevents us from changing the boot code itself. - SHA1 hash: CD, CE, CG. These hashes are contained in the RSA signed part of the previous sections and we can therefore not break it (also not time attackable). These can essentially be seen as extentions of the RSA signatures in CB and CF. Again preventing us from modyfing the boot code itself. - SHA1-HMAC authentication. This is done in CB and CF too (but your CPU has the key). This prevents you to choose between released versions of the boot sections/dash etc. However this was time attackable.
Dump Data
There are 3 essential parts of data you want to dump from the Xbox 360; the NAND flash, the fusesets, and the 1BL first bootloader. The former located in the HYNIX HY27US08281A flash and the two latter in the IBM PowerPC Xeon CPU.
NAND
There are two ways to get the NAND flash:
- Physically read the flash using the Infectus NAND Microchip Flasher
- Dump it from memory using the King Kong Exploit and Linux
Fusesets and 1BL
These two can only be dumped using Linux. Follow the 'Linux' section below to extract the parts.
Dumping
Infectus
Linux
Start by upgrading to a vulnerable kernel, 4532 or 4548, and patch the King Kong game ISO to load the XeLL loader from a LiveCD, here.
There are two different ways to dump the necessary data, one with dump32 to get the 1BL, CPU Key and NAND dump, and the other tmbincdump to get the true NAND dump with the correct ECC values.
dump32
When Linux is loaded, start one of the webbrowsers (assuming you have a network cable plugged in) and browse to this page to download arnezami's dump32.c (mirror). Save it to the desktop.
Open a new Terminal from the menus, and 'cd Desktop'. Now compile the dump32 using the following command:
gcc -o dump32 dump32.c
As shown, now execute the application by typing 'sudo ./dump32'. Make sure to make it executable by typing 'chmod +x' first. The application will now dump the fuses, 1bl and NAND to the current directory.
sudo ./dump32
Backup these files to another computer through SCP, USB pen, website upload, FTP transter, or similar. I used SCP to another Mac OS X machine:
scp 1BL.BIN FUSES.TXT NAND.BIN torsten@192.168.1.3:
To SCP in from a Windows machine, download WinSCP and set a password for the root account with 'sudo passwd' and enter a password. Find the IP address of the 360 using the network tool from the menus.
tmbincdump
Get the tmbinc code (mirror) and save it to the desktop as tmbincdump.c. You have to change the writereg command from:
writereg(COMMAND, 2);
to:
writereg(COMMAND, 3);
This enables the correct mode to dump the NAND flash. Mode 2 shows all the blank and empty banks, while mode 3 only dumps the necessary data and auto corrects for bad blocks.
Compile it using:
gcc -I=/usr/include/ -O -o tmbincdump tmbincdump.c
Now execute the dumper:
sudo ./tmbincdump
The complete dump will be saved to a file named tmbincdump.bin. Transfer this to a computer using one of the methods referred to
View Content
To view the content of the dumped NAND flash download the latest version of 360 Flash Dump Tool and open the BIN file.
To decode all of the encrypted content you need the CPU Key located in the fusesets and the 1BL Key located in the CPU ROM. These are found using the King Kong shader exploit and XeLL (Xeon Linux Loader) on vulnerable firmware version, e.g 4532 and 4548, as shown above.
1BL Key
The 1BL is the 'First Boot Loader' and is stored in the ROM inside the CPU. The loader is 32KB and the 1BL key is the same for all Xbox 360 machines. To dump the 1BL you need to compile dump32.c and execute it to extract fuses.txt, nand.bin and 1bl.bin.
Due to the nature of the legality behind the static key, you have to find it yourself (think AACS). To find the key inside 1bl.bin you need to install IDA and disassemble using the PPC processor setting.
Discover the 1BL key [4]:
Start at sub_4240 and remember that encrypted data is at 0x8000_0200_C800_0000 and destination of unencrypted data is 0x8000_0200_0001_0000 and key is 0x10 bytes long. %rtoc is 0. Don't get sidetracked digging too deeply into each and every bl off sub_4240.
To figure out if you've found the correct key, open 360 Flash Dump Tool, enter the key, and check if there's a 'Pairing Data' entry.
Fuses
There are 12 fusesets and they form the fundament for the Xbox 360 hypervisor security [5]. The fusesets (12) are located inside the CPU and thus hard to modify externally.
Fuseset #01 - 00: c0ffffffffffffff Fuseset #02 - 01: 0f0f0f0f0f0f0ff0 Fuseset #03 - 02: 0f00000000000000 Fuseset #04 - 03: xxxxxxxxxxxxxxxx Fuseset #05 - 04: xxxxxxxxxxxxxxxx Fuseset #06 - 05: yyyyyyyyyyyyyyyy Fuseset #07 - 06: yyyyyyyyyyyyyyyy Fuseset #08 - 07: 0000000000000000 Fuseset #09 - 08: 0000000000000000 Fuseset #10 - 09: 0000000000000000 Fuseset #11 - 0a: 0000000000000000 Fuseset #12 - 0b: 0000000000000000
For a description of what the purpose of each set, see this thread post.
CPU / Per-Box Key
The CPU Key is used to only encrypt the Keyvault (which is then encrypted by the 1BL Key). By altering the the Keyvault you can change the lockdown counter on a vulnerable kernel, re-encrypting the Keyvault with the CPU Key, and downgrading to vulnerable kernel by flashing the NAND. A prior NAND dump from a vulnerable kernel is still needed and you have to already acquired the CPU Key using the King Kong exploit.
It is now possible to downgrade to a vulnerable kernel by time attacking the hash value of the lockdown counter. The counter is unsigned and the hash is compared bytewise.
The CPU Key can be found by combining fusetset #03 + #05 (or #04 + #06). The final string should be 16 bytes long, e.g xxxxxxxxxxxxxxxxyyyyyyyyyyyyyyyy.
To extract the fusesets use XeLL (shown below) or arnezami's dump32.
XeLL Output
This shows the XeLL output from the serial cable method.
Xe>! XeLL - Xenon linux loader 0.1 * clearing BSS... * Attempting to catch all CPUs... CPUs online: 01.. CPUs online: 15.. * success. trying to initialize network... ok now the NIC NETIF at 8000000001459478 NIC reset reset: 01805508 1478 before: f2050000 1478: f2050000 init tx init rx starting httpd server..ok! * CPU PVR: 00710200 * FUSES - write them down and keep them safe: fuseset 00: c0ffffffffffffff fuseset 01: 0f0f0f0f0f0f0ff0 fuseset 02: 0f00000000000000 fuseset 03: c2666e8fab3c299a fuseset 04: c2666e8fab3c299a fuseset 05: c49a457d64ba4b3d fuseset 06: c49a457d64ba4b3d fuseset 07: f000000000000000 fuseset 08: 0000000000000000 fuseset 09: 0000000000000000 fuseset 10: 0000000000000000 fuseset 11: 0000000000000000
Keyvault
The Keyvault contains unsigned information about the system, like serial number, manufacture date, DVD key, certificates, etc. It's encrypted by the CPU Key.
Downgrade
Downgrading is restricted by changing a lockdown counter in the NAND and the value of a fuseset. If these two don't match, e.g lockdown counter is lower than the value of the fuseset, the machine refuses to boot. It's possible to disable the change of the fuseset by removing power the the fuse and essentially disabling it. More about how to remove the R6T3 resistor.
It is still possible to downgrade if the fuseset has increased, but it requires CPU Key and altering of the old NAND dump to increase the lockdown counter. (As of 9th Aug. 2007 the CPU Key can only be found on a exploitable 4532 or 4548 system).
Counters
While upgrading to 4532 or 4552, fuseset #07 is changed and the lockdown counter in the NAND is increase by 1, for each update. I.e.:
Stock 2241: Lockdown counter: 0 Applied 4532: Lockdown counter: 1 Fuseset 07: f000000000000000 Applied 4552 Lockdown counter: 2 Fuseset 07: ff00000000000000
Fix lockdown counter
You can't directly flash a 4532 dump after updating to 4552. The fuseset has increased and the 4532 dump will not boot if the lockdown counter is lower than the fuseset, i.e refuses to boot if lockdown count > fuseset count.
To bypass this you need to decrypt the CF section of the 4532 dump and change the byte at 0x21F to something higher. The 360 Flash Dump Tool will patch and properly re-encrypt the flash image.
Region code
It's possible make a PAL system act as a NTSC system, and vice versa, by changing the region bit in the Keyvault [6].
1. Dump the NAND from the US 360 (528-bytes-per-page) 2. Open in the latest flashtool (v0.8 ) and click [extract] 3. Edit extracted KV.bin and change 16-bits at offset 0xB8 from 0x00FF (NTSC) to 0x02FE (PAL) 4. Open in flashtool and click [patch], check the "patch keyvault" box and select the KV.bin modified in step 3 5. Click [OK] and choose output file 6. Flash output image back to the NAND of the US 360 7. Try an EU game or two.
Apparently you need both the 1BL and CPU Key to perform this with 360 Flash Dump Tool v0.8.
Region codes [7]:
- PAL : il faut changer ces 4 chiffres en 02FE - NTSC/J : il faut changer ces 4 chiffres en 01FF - NTSC-U/C : il faut changer ces 4 chiffres en 00FF - NTSC/KOR : il faut changer ces 4 chiffres en 01FC
Future hacks
- Downgrade allowed via timing attack for all current machines, as of 2007-08-19 / kernel 5766 [8]
- Dual kernels via switches or xD cards, one for exploitable kernel (4532 or 4548), another for Xbox Live/latest kernel
- King Kong game required to boot homebrew
- Find kernel exploits in 4532 or 4548 to make an on-boot exploit to not require King Kong
References
- Unsigned code on modded/hacked 360?
- How To: Dumping 1BL & Fuse Data from Linux
- 360 Flash Dump Tool V0.1
- Downgrade Possible if CPU Key is Known
- Probutus' NAND tool
- Pec's flash dump tool
- arnezami's dump32.c dump tool
- tmbinc's flash read dump tool
- atiman edition of tmbinc's dump tool
- Keyvault encrypted by CPU Key
- Keyvault Content
- Keyvault decrypted by Hypervisor
- Changing DVD Key and Region code
- Timing Attack - Stupid Question
- Eurasia Xbox 360 Wiki
- Layout of the 16mb NAND
- Change region code