Difference between revisions of "WEP Cracking"
| Line 33: | Line 33: | ||
* '''Key attack''': | * '''Key attack''': | ||
# Find Initialization Vector collisions where two cipher texts (12-bytes ARP) are the same (only 2^24 possibilities) | # Find Initialization Vector collisions where two cipher texts (12-bytes ARP) are the same (only 2^24 possibilities) | ||
# XOR | # Reverse XOR on first 12-bytes using the known plain-text ARP data | ||
# RC4 stream cipher is revealed for that specific | # RC4 stream cipher is revealed for that specific Initialization Vector | ||
# Find enough collisions | # Find enough collisions | ||
# Data used to build a table of Initialization Vectors and RC4 stream ciphers | # Data used to build a table of Initialization Vectors and RC4 stream ciphers | ||
Revision as of 00:54, 27 August 2009
WEP is infamously known as the totally broken wireless security protocol. Severe misapplication of cryptographic primitives were discovered in 2001 and after several cascading discoveries afterwards, it's now possible to crack a WEP protected network in under a minute. WPA is the successor to WEP and features a better but not perfect security protocol.
Background
There are now many sources that describe the vulnerability in detail and APR replay to generate traffic, but this is a short summary. For an throughout explaination on how WEP is implemented and the vulnerabilities, see the link below.
Types attacks:
- Passive attacks to decrypt traffic based on statistical analysis.
- Active attack to inject new traffic from unauthorized mobile stations, based on known plaintext.
- Active attacks to decrypt traffic, based on tricking the access point.
- Dictionary-building attack that, after analysis of about a day's worth of traffic, allows real-time automated decryption of all traffic.
Original discoveries and paper:
- (In)security of the WEP algorithm by Nikita Borisov, Ian Goldberg, and David Wagner
- Intercepting Mobile Communications:The Insecurity of 802.11 paper
Way of attack
This is the most efficient method to crack a WEP protected network. The attack can be performed in under a minute. The result is the WEP hex/ascii-key used.
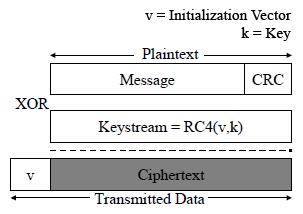
- WEP encryption:
- 24-bit unencrypted initialization vector + 104-bit key (13 characters/bytes), 128-bit key
- Used to generate RC4 cipher stream
- XOR the message
- Encrypted network frame
- ARP replay:
- On the basis that the first 12-bytes of ARP packets always stays the same
- Capture one ARP packet
- Continously inject packet back to into the network to stimulate traffic
- Capture 10-20 000 ARP (or other data) packets
- Key attack:
- Find Initialization Vector collisions where two cipher texts (12-bytes ARP) are the same (only 2^24 possibilities)
- Reverse XOR on first 12-bytes using the known plain-text ARP data
- RC4 stream cipher is revealed for that specific Initialization Vector
- Find enough collisions
- Data used to build a table of Initialization Vectors and RC4 stream ciphers
- Use table to gain a statistical factor for the remainder missing key bytes, 104-bit (13 character) key